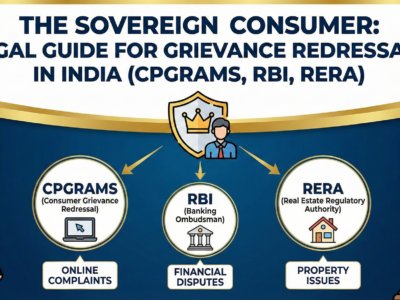
The unauthorized publication of a private video is a profound violation, leaving victims feeling powerless and exposed in the digital world. This guide from eVaakil.com is designed to change that. It is a comprehensive, step-by-step resource that demystifies India’s legal landscape for victims of non-consensual image abuse. Here, you will find a clear roadmap to justice—from understanding your fundamental Right to Privacy to the specific criminal laws you can invoke, the civil remedies you can seek, and the practical playbook you must follow to take back control, hold perpetrators accountable, and begin the process of recovery.
Your Digital Legal Guide
A Comprehensive Legal Guide to Non-Consensual Video Publication in India
Rights, Recourse, and Responsibilities in the Digital Age.
Part I: The Constitutional Bedrock – The Right to Privacy
The entire legal framework governing the non-consensual use of personal media in India is anchored in a powerful constitutional principle: the fundamental Right to Privacy. In the historic Justice K.S. Puttaswamy v. Union of India judgment, the Supreme Court unanimously declared that privacy is an intrinsic and inseparable part of the Right to Life and Personal Liberty guaranteed under Article 21 of the Constitution. This elevated privacy from a mere common law right to a constitutionally protected guarantee, essential for human dignity.
The Three Facets of Privacy
Spatial Control
The right to control one's own private spaces. Privacy goes with a person, not a place.
Decisional Autonomy
The right to make intimate personal choices without coercion (e.g., marriage, family life).
Informational Self-Determination
The right to control the collection, processing, and sharing of one's personal data, including videos.
The act of uploading a video without consent is a direct violation of informational self-determination. The Puttaswamy judgment created a positive obligation on the state to protect individuals from such violations by non-state actors, paving the way for the Digital Personal Data Protection Act, 2023.
Part II: The Data Protection Framework
India's data protection laws provide the statutory backbone for regulating personal digital media.
The Digital Personal Data Protection (DPDP) Act, 2023
The DPDP Act is India's first comprehensive data privacy law. Its cornerstone is consent, which must be free, specific, informed, and unambiguous, given through a clear affirmative action. Before processing data (i.e., uploading a video), the uploader ("Data Fiduciary") must inform the person in the video ("Data Principal") of the specific purpose. A key right for victims is the ability to withdraw consent at any time, which obligates the uploader to erase the data. While the Act has an exemption for "personal or domestic purpose," its application to viral social media content is yet to be tested in courts.
The Information Technology (IT) Act, 2000 & SPDI Rules, 2011
Prior to the DPDP Act, Section 43A of the IT Act and the SPDI Rules governed data protection, primarily holding corporate bodies liable for negligence in handling "sensitive personal data." While the DPDP Act is now the principal law, these provisions remain relevant, especially Section 72A, which criminalizes the disclosure of personal information obtained under a lawful contract without consent.
Part III: Criminal Liability – Offences and Penalties
Indian law provides a multi-layered arsenal of criminal provisions against non-consensual video publication, found in both the IT Act and the Indian Penal Code (IPC).
Key Offences under the IT Act, 2000
- Section 66E (Violation of Privacy): Directly criminalizes capturing, publishing, or transmitting an image of a person's "private area" without consent. (Penalty: Up to 3 years imprisonment or ₹2 lakh fine).
- Section 67 (Obscene Material): Penalizes publishing "lascivious" material that tends to "deprave and corrupt." (Penalty: Up to 3 years imprisonment and ₹5 lakh fine).
- Section 67A (Sexually Explicit Material): A stricter provision for material containing "sexually explicit acts." (Penalty: Up to 5 years imprisonment and ₹10 lakh fine).
Key Offences under the Indian Penal Code (IPC), 1860
- Section 354C (Voyeurism): Criminalizes a man watching or capturing an image of a woman in a "private act." Crucially, it also criminalizes the dissemination of an image even if it was captured consensually. This directly targets "revenge porn." (Penalty: 1-3 years for first offence, 3-7 for subsequent).
- Section 354D (Stalking): Includes monitoring a woman's use of the internet or email despite her disinterest (cyberstalking).
- Sections 499/500 (Criminal Defamation): Applies if the video harms the victim's reputation.
| Provision | Key Feature | Gender Specificity |
|---|---|---|
| Sec. 66E, IT Act | Focuses on "private areas" | Neutral |
| Sec. 354C, IPC | Covers dissemination after consensual capture | Male accused, Female victim |
| Sec. 67A, IT Act | Highest penalties for explicit content | Neutral |
Part IV: Civil Liability – Seeking Damages and Injunctions
Parallel to criminal action, a victim can file a civil lawsuit to seek monetary compensation (damages) and court orders (injunctions) to stop the video's spread. This is based on the law of torts, specifically the torts of defamation and invasion of privacy.
The most powerful tool in a civil suit is the injunction. A victim can seek an immediate interim injunction to have the video taken down from all platforms while the case proceeds. If successful at trial, a permanent injunction will be granted. Courts can also award substantial damages to compensate for reputational harm and emotional distress.
Part V: A Victim's Playbook – Practical Steps for Redressal
Facing non-consensual publication is traumatic, but a structured and swift response is key to regaining control. Here’s a step-by-step guide on what to do.
Preserve Evidence
Immediately take screenshots/recordings (with URL, date, time visible). Save links. Download the video. Do not engage with the perpetrator.
Report to Platforms
Use the platform's reporting tools (e.g., YouTube's Privacy Complaint, Facebook's "Report Harassment"). Cite the IT Rules, 2021, which mandate takedown within 24 hours.
File a Cyber Crime Complaint
File a complaint online at www.cybercrime.gov.in or call the helpline 1930. This initiates a formal police investigation.
Consult a Lawyer
Engage a lawyer to send a legal notice to the perpetrator, file an FIR at a police station if required, and/or file a civil suit for an immediate injunction and damages.
What to Expect After Reporting to the Police
Once you file an FIR, an Investigating Officer (IO) will be assigned to your case. The police will issue a formal notice to the social media platform to preserve all data related to the offending account. Their cyber cell will then work to trace the IP address of the uploader to identify the perpetrator. It is important to stay in touch with the IO for updates on the investigation. You have the right to receive a copy of your FIR free of cost.
Part VI: Defenses and Nuances
The legality of filming and publishing is context-dependent. The right to privacy must be balanced against the right to freedom of speech. A key legal standard is the "reasonable expectation of privacy," which can exist even in public places. A person having a private conversation in a park corner has a higher expectation of privacy than someone giving a public speech.
In defamation cases, a defendant can argue that the video's content is true and its publication was for the public good (e.g., exposing corruption). Journalists may also claim newsworthiness, but courts distinguish between what is in the "public interest" versus what is merely "of interest to the public."
Part VII: The Role of Intermediaries – Holding Platforms Accountable
Social media platforms, search engines, and internet service providers are legally termed "intermediaries." While they are granted "safe harbour" protection under Section 79 of the IT Act (meaning they are not automatically liable for user-generated content), this protection is conditional on them following specific due diligence requirements laid out in the Information Technology (Intermediary Guidelines and Digital Media Ethics Code) Rules, 2021.
Mandatory Takedown Timelines
The IT Rules, 2021, impose strict timelines on intermediaries for acting on complaints. This is a critical tool for victims seeking immediate relief.
Complaint of Nudity or Sexual Act
If your complaint involves content showing you in a state of nudity or in a sexual act.
Platform must take down the content within 24 hours.
For other types of unlawful content (e.g., defamatory), intermediaries must acknowledge the complaint within 24 hours and resolve it within 15 days. Failure to comply can result in the loss of their safe harbour status, making them liable for prosecution.
Part VIII: Special Protections for Children – The POCSO Act
When the victim is a minor (below 18 years of age), the case attracts the stringent provisions of the Protection of Children from Sexual Offences (POCSO) Act, 2012. This is a special law that provides enhanced protection for children and stricter punishments for offenders.
Using a child for pornographic purposes is a specific offence under Section 14 of the POCSO Act, with a minimum punishment of 5 years imprisonment. The law also mandates a child-friendly judicial process.
Key Protections under POCSO: A child's statement must be recorded by a woman police officer, not in uniform, at the child's residence. The identity of the child cannot be disclosed by the media, and the trial must be completed within one year.
All proceedings under POCSO are held in-camera (not in open court) and the identity of the child is protected from disclosure.
Part IX: Evidence & Procedure in the Digital Age
In a cybercrime case, your evidence—screenshots, downloaded videos, chat logs—is electronic. To be admissible in court, electronic evidence must be authenticated. This is done through a certificate under Section 65B of the Indian Evidence Act, 1872.
The Crucial Section 65B Certificate
This is a signed declaration by the person who produced the electronic record (e.g., the person who took the screenshot from their phone). It certifies that the electronic record was produced by a computer that was operating properly and that the content has not been tampered with.
Without this certificate, the court may refuse to consider your most critical evidence.
Part X: Frequently Asked Questions (FAQ)
Q: What if the video was taken with my consent but published without it?
A: This is still an offence. Consent to capture is not consent to publish. Section 354C of the IPC (Voyeurism) explicitly covers the dissemination of images/videos even if they were captured consensually. You also have remedies under the IT Act and civil law for breach of privacy.
Q: The perpetrator is anonymous or using a fake profile. What can I do?
A: Law enforcement agencies, through their cyber cells, have tools to trace IP addresses and identify anonymous users. When you file an FIR, the police can legally compel social media platforms and internet service providers to disclose the details of the account holder.
Q: What if the person who published the video lives in another country?
A: The IT Act, 2000 has extra-territorial jurisdiction (Section 75). This means if the act affects a person or computer resource in India, Indian law can apply. However, enforcement is complex and often requires international cooperation through treaties like a Mutual Legal Assistance Treaty (MLAT).
Q: Can I file a criminal case and a civil case at the same time?
A: Yes. The two proceedings are independent. The goal of a criminal case is to punish the offender (jail, fine), while the goal of a civil case is to get compensation (damages) and prevent further harm (injunction). They can run parallel to each other.
Part XI: Emerging Threats – AI, Deepfakes, and Morphing
Technological advancements have introduced new forms of harassment, with AI-generated deepfakes and morphed images posing a significant threat. These are synthetic media where a person's likeness is convincingly replaced with someone else's, often used to create fake pornographic or compromising videos.
How Deepfakes Work
1. Input Data
An AI algorithm is fed many images/videos of the target person (e.g., from their social media).
2. AI Processing
The AI learns to map the target's facial features onto a source video, creating a synthetic output.
3. Fake Video Output
A realistic but entirely fabricated video is created, which can be used for malicious purposes.
Legal Recourse for Deepfakes
While India does not yet have a specific "deepfake law," victims are not without recourse. A deepfake video can be prosecuted under a combination of existing laws:
- Defamation (Sec 499, IPC): If the video harms the victim's reputation.
- Publishing Obscene/Sexually Explicit Material (Sec 67/67A, IT Act): If the deepfake is pornographic.
- Identity Theft (Sec 66C, IT Act): For fraudulently using someone's electronic signature, password or other unique identification feature.
- Cheating by Personation (Sec 66D, IT Act & Sec 419, IPC): If the deepfake is used to deceive someone for personal gain.
The primary challenge with deepfakes is attribution—proving who created it. This often requires sophisticated forensic analysis by cyber police.
Part XII: The Jurisdictional Maze in Cyberspace
One of the most complex questions in cybercrime is: "Where do I file my complaint?" If the victim is in Mumbai, the perpetrator is in Delhi, and the server hosting the video is in another country, which police station or court has the authority to act?
The Power of Extra-Territorial Jurisdiction
The Information Technology Act, 2000, provides a powerful solution in Section 75. It grants the Act extra-territorial jurisdiction. This means that the law applies to any offence or contravention committed outside India by any person, irrespective of their nationality, if the act involves a computer, computer system, or computer network located in India.
Jurisdiction Simplified
If the effect of the crime is felt in India, Indian law can apply.
An FIR can be filed with the cyber police in the city where the victim resides and suffered harm.
This means a victim can typically file an FIR with their local police or cybercrime cell, as the "cause of action" (the harm) occurred where they are located. While prosecuting offenders in other countries is challenging, this provision ensures that the legal process can at least be initiated in India.
Part XIII: Landmark Judgments – How Courts See It
Judicial precedent plays a critical role in shaping how laws are applied. Here are a few landmark cases that have defined the legal landscape for privacy and online content in India.
Justice K.S. Puttaswamy (Retd.) v. Union of India (2017)
Supreme Court of India
Principle: This monumental judgment established the Right to Privacy as a fundamental right under Article 21 of the Constitution. It forms the bedrock of all privacy-related claims, stating that privacy includes decisional autonomy and the right to control the dissemination of personal information.
Impact: Every case of non-consensual video publication is fundamentally a violation of this right.
Shreya Singhal v. Union of India (2015)
Supreme Court of India
Principle: While this case is famous for striking down the vague Section 66A of the IT Act, it also clarified the scope of intermediary liability. It upheld the safe harbour principle but emphasized that intermediaries must take down content upon receiving an actual court order or a notification from a government agency.
Impact: It defined the process for legally mandating takedowns, reinforcing the responsibilities of platforms.
Part XIV: Beyond the Courtroom – Support Systems & Resources
Navigating the legal system is only part of the battle. The emotional and psychological toll of such violations can be immense. It is crucial to seek support from specialized organizations and mental health professionals.
National Commission for Women (NCW)
A statutory body that takes up cases of violence and harassment against women. They have a dedicated cybercrime cell.
File a Complaint →National Cyber Crime Reporting Portal
The official government portal to report all types of cybercrime, including those against women and children.
Report Anonymously →Internet Freedom Foundation (IFF)
An Indian digital liberties organization that provides legal assistance in select cases of online harassment and privacy violations.
Get Help →Mental Health Support
Organizations providing free and confidential counseling services. It is vital to care for your mental well-being.
National Mental Health Helpline: KIRAN (1800-599-0019)
Part XIV: Corporate & Workplace Liability – The POSH Act
When non-consensual image publication occurs in a professional context—for instance, if a colleague shares an intimate video of another employee in a work-related group—it can constitute a severe form of workplace sexual harassment. Employers have a legal and ethical duty to provide a safe working environment.
The Sexual Harassment of Women at Workplace (POSH) Act, 2013
The POSH Act is a specific law designed to prevent and address sexual harassment at the workplace. The act of sharing non-consensual intimate images or videos falls squarely within the definition of sexual harassment, which includes "any other unwelcome physical, verbal or non-verbal conduct of sexual nature."
Employer's Mandatory Obligations
Form an Internal Committee (IC)
Every organization with 10 or more employees must constitute an IC to investigate complaints.
Create a POSH Policy
Draft and widely publicize a policy against sexual harassment, detailing the complaint procedure.
Conduct Awareness Programs
Regularly train employees on what constitutes sexual harassment and the recourse available.
A victim can file a complaint with their company's IC. The IC has powers similar to a civil court to conduct an inquiry. If the complaint is proven, the IC can recommend actions like termination of the perpetrator's employment and monetary compensation for the victim. Failure to comply with the POSH Act can lead to hefty fines for the employer.
Part XV: The Extortion Angle – When Blackmail Meets Abuse (Sextortion)
Often, the non-consensual publication of intimate media is not the primary goal but a threat used for blackmail. This crime, commonly known as "sextortion," involves a perpetrator threatening to release private and sensitive material unless the victim complies with their demands—which could be for money, more sexual images, or other actions against their will.
The Crime of Extortion: Section 383 & 384 of the IPC
Sextortion is a form of criminal extortion. Under Section 383 of the Indian Penal Code, extortion is defined as intentionally putting a person in fear of injury and thereby dishonestly inducing them to deliver any property or valuable security.
Applying it to Sextortion: The "fear of injury" includes the fear of injury to one's reputation. Threatening to release a private video to ruin someone's reputation unless they pay money is a textbook case of extortion. The punishment under Section 384 can be imprisonment for up to 3 years, a fine, or both.
If you are a victim of sextortion, it is critical to report it to the police immediately. Do not give in to the demands, as this often emboldens the perpetrator to ask for more. Preserve all communication (chats, emails, phone numbers) as evidence.
Part XVI: Proactive Defence – A Guide to Digital Hygiene
While the law provides recourse after an incident, proactive measures can significantly reduce the risk of becoming a victim. Practicing good "digital hygiene" is the first line of defence in protecting your private information.
Review Social Media Privacy Settings
Set your profiles to "Private." Limit who can see your posts, friends list, and personal information. Be cautious about accepting friend requests from unknown individuals. Avoid oversharing location data.
Use Strong, Unique Passwords & 2FA
Use a password manager to create complex passwords for each account. Enable Two-Factor Authentication (2FA) on all critical accounts (email, social media, banking) for an extra layer of security.
Be Wary of Phishing and Malware
Do not click on suspicious links or download attachments from unknown senders. These can install spyware on your devices, giving hackers access to your camera, microphone, and files.
Secure Your Devices
Always lock your phone and computer with a strong passcode, PIN, or biometric lock. Encrypt your hard drive. Ensure your software and apps are always updated to patch security vulnerabilities.
Part XVII: The Aftermath – Reputation Management & The Right to be Forgotten
Even after a video is taken down from its original source, it can persist in search engine caches, archives, and on obscure websites. Managing the long-term impact on your digital reputation is a critical final step in the recovery process.
The Right to be Forgotten (RTBF)
The "Right to be Forgotten" is an emerging legal concept in India, supported by several High Court rulings and flowing from the fundamental Right to Privacy. It allows an individual to request the removal of their personal data from the internet, particularly if it is no longer necessary, relevant, or is causing them harm.
While not yet an absolute right codified in law, you can approach the courts with a writ petition to direct search engines like Google to "de-index" or de-link harmful URLs from search results associated with your name. This doesn't delete the content from the source website, but it makes it incredibly difficult for the general public to find.
Practical Steps for Online Reputation Management
- Google Search Console: Use Google's "Remove outdated content" tool to request the removal of pages from search results that have already been deleted from the source website but still appear in search.
- Contact Search Engines: Formally write to the grievance officers of search engines, citing court orders (if any) and your Right to Privacy, requesting the de-indexing of specific harmful URLs.
- Build a Positive Online Presence: Proactively create positive and professional content associated with your name (e.g., a LinkedIn profile, a personal blog, or participation in online forums). Over time, this can push negative results further down the search rankings, a technique known as Search Engine Reputation Management (SERM).
Part XVIII: The Courtroom Experience – Victim Protection & Judicial Sensitivity
Facing the accused in court can be a daunting and re-traumatizing experience for a victim. The Indian legal system has specific provisions to protect the dignity and privacy of victims in sexual offence and privacy violation cases.
Key Protections for Victims During Trial
In-Camera Proceedings
Under Section 327 of the CrPC, trials for offences like voyeurism (354C) are conducted "in-camera." This means the public and media are excluded from the courtroom. Only the judge, court staff, parties involved, and their lawyers are present, creating a more private and less intimidating environment for the victim to testify.
Anonymity of the Victim
Section 228A of the IPC makes it a criminal offence to print or publish the name or any matter which may make known the identity of a victim of sexual offences. This legal shield is crucial in preventing further public harassment and social stigma.
Victim Compensation Schemes
Section 357A of the CrPC mandates that every state government must have a scheme for providing funds for the purpose of compensation to victims. The court can recommend compensation to help the victim with medical expenses, psychological counseling, and other rehabilitation needs.
Sensitive Questioning
The judiciary is increasingly trained to handle such cases with sensitivity. Indecent or scandalous questions are not permitted during cross-examination, and judges are expected to protect the victim from character assassination by the defence counsel.
Part XIX: Following the Money – Financial Trails in Sextortion
In sextortion cases, the perpetrator's greed is often their biggest weakness. The demand for money creates a financial trail that can be a powerful tool for law enforcement to identify and prosecute them, even if they use fake profiles online.
How Financial Evidence is Traced
When a victim is coerced into paying money, the transaction leaves a digital footprint that investigators can follow:
- UPI/Digital Wallet Transactions: Police can obtain the KYC (Know Your Customer) documents linked to the UPI ID or wallet number from the service provider (e.g., PayTM, Google Pay). This often reveals the perpetrator's real name, phone number, and linked bank account.
- Bank Account Transfers (NEFT/IMPS): A notice to the receiving bank can reveal the account holder's identity, address, and transaction history, which might lead to other victims or accomplices.
- Cryptocurrency Wallets: While more complex, tracing cryptocurrency is not impossible. Police can analyze the blockchain and work with crypto exchanges to identify when the illicit funds are cashed out into a bank account, revealing the perpetrator's identity.
The Role of I4C: The Indian Cyber Crime Coordination Centre (I4C), under the Ministry of Home Affairs, has a 'National Cybercrime Financial Fraud Reporting and Management facility' that helps in tracking and blocking illicit financial flows in real-time.
Part XX: Crossing Borders – The International Legal Maze
What happens when the offender is in another country? The internet's borderless nature presents the biggest challenge to cybercrime investigation. While Section 75 of the IT Act gives India extra-territorial jurisdiction, enforcing it requires international cooperation.
Tools of International Cooperation
Mutual Legal Assistance Treaty (MLAT)
This is a formal treaty between two countries to exchange information and provide assistance in criminal investigations. India has MLATs with over 40 countries, including the USA, UK, and Canada. The police can send a request through the Ministry of Home Affairs to get user data from a foreign company or to have a suspect investigated by foreign police.
Letters Rogatory (LR)
If no MLAT exists, a court in India can issue an LR, which is a formal request to a foreign court for judicial assistance. This is a more time-consuming process but is a standard diplomatic channel for evidence gathering.
Interpol Notices
For serious offenders, Indian law enforcement can request Interpol to issue notices. A Red Notice is a request to law enforcement worldwide to locate and provisionally arrest a person pending extradition, surrender, or similar legal action.
Part XXI: A Global Perspective – How India's Laws Compare
Non-consensual image abuse is a global problem, and different countries have adopted different legal strategies to combat it. Here’s a brief comparison of India's approach with other major jurisdictions.
| Jurisdiction | Legal Approach | Key Feature |
|---|---|---|
| India | "Patchwork" approach using various sections of the IPC and IT Act (e.g., Voyeurism, Obscenity, Defamation). | Comprehensive but lacks a single, specific "revenge porn" offence, which can sometimes lead to ambiguity. |
| United Kingdom | Specific criminal offence created under the Criminal Justice and Courts Act 2015 for disclosing private sexual photographs and films without consent. | Clear, targeted legislation that focuses on the intent to cause distress, making prosecution more straightforward. |
| United States | No federal law. A mosaic of state laws with varying definitions and penalties. Intermediaries have strong protection from liability under Section 230 of the Communications Decency Act. | Highly fragmented legal landscape. The strong "safe harbour" for platforms makes holding them accountable more difficult than in India. |
| European Union | The General Data Protection Regulation (GDPR) treats personal images as protected data. Non-consensual processing (publication) is a major violation. Many member states also have specific criminal laws. | A strong, data-protection-centric approach with a powerful "Right to Erasure" that is legally binding on platforms. |
Part XXII: The Evolving Judiciary – Interpreting Old Laws for New Crimes
Many of India's foundational laws, like the Indian Penal Code, were written in an era unimaginable to today's digital reality. A key aspect of combating modern cybercrimes has been the proactive and purposive interpretation of these laws by the Indian judiciary.
Judicial Activism in Defining "Privacy" and "Dignity"
Courts have moved beyond literal interpretations to address the real-world harm of online abuse. For example, the concept of a woman's "modesty" has been judicially expanded to include her digital persona and her right to control her own image. The judiciary has repeatedly affirmed that an attack on a person's digital identity is as severe as a physical one.
Principle of Purposive Interpretation: Judges often apply this principle, asking, "What was the purpose of the law?" For instance, the purpose of laws against obscenity and voyeurism was to protect individual dignity. The courts have held that this purpose applies with even greater force in the online world, where harm is amplified and permanent.
Part XXIII: Digital Forensics Deep Dive – The Science of Evidence
Digital evidence is fragile and can be easily altered. The process of collecting, preserving, and analyzing it in a manner that is admissible in court is a specialized science known as digital forensics.
Key Concepts in Digital Forensics
Hash Value (Digital Fingerprint)
When evidence (like a video file) is seized, a unique alphanumeric string called a "hash value" is generated from it. Any change to the file, even a single pixel, will completely change its hash value. This is used in court to prove that the evidence presented is the exact same as what was seized and has not been tampered with.
Chain of Custody
This is a meticulous chronological record of the digital evidence. It documents who handled the evidence, when, and for what purpose, from the moment of seizure to its presentation in court. A broken chain of custody can render the evidence inadmissible.
Data Recovery from Deleted Files
When you "delete" a file, the data is often not immediately erased. The operating system simply marks the space as available to be overwritten. Forensic tools can often recover these "deleted" files, which can be crucial in proving a perpetrator's guilt.
Part XXIV: The Intersectional Lens – Compounded Vulnerabilities
The harm from non-consensual image abuse is not experienced uniformly. A victim's social identity—based on caste, religion, sexual orientation, disability, or economic status—can profoundly compound the trauma and create additional barriers to accessing justice.
For instance, a woman from a marginalized caste may face not just gendered shaming but also caste-based slurs and threats. A member of the LGBTQ+ community may be "outed" against their will, facing social ostracism and familial rejection in addition to the privacy violation. These intersectional factors can lead to:
- Increased Stigma: Victims may fear that the abuse will be used to reinforce existing prejudices against their community.
- Barriers to Reporting: Fear of disbelief, discrimination, or insensitive treatment from law enforcement can deter victims from filing complaints.
- Lack of Family Support: Victims from conservative backgrounds may face blame and isolation from their own families.
It is imperative for the justice system, support organizations, and society at large to adopt an intersectional approach that recognizes and addresses these unique and compounded vulnerabilities.
Part XXV: The Future of Digital Safety – A Legislative Roadmap
While India's current legal framework is adaptable, there are gaps that future legislation could address to make the fight against digital abuse more effective. The proposed Bharatiya Nyaya Sanhita (BNS), which aims to replace the IPC, is a step in this direction, but more can be done.
Potential Legislative & Policy Reforms
A Specific Offence for NCII
Creating a single, specific, and technology-neutral criminal offence for "Non-Consensual Creation or Distribution of Intimate Images" (NCII) would eliminate ambiguity and ensure consistent application of the law.
Regulating AI and Deepfake Tools
Laws requiring developers of generative AI tools to implement safeguards, such as watermarking synthetic media or banning the creation of non-consensual explicit content, are being debated globally.
Strengthening the Right to Erasure
Codifying a strong, clear, and easily enforceable "Right to Erasure" under the DPDP Act rules would empower victims to remove their data without always needing to resort to a lengthy court process.
Mandatory Digital Literacy
Introducing mandatory, age-appropriate digital literacy and online safety education in school curricula can serve as a long-term preventative measure.
Part XXVI: The Fourth Estate's Duty – Media Ethics in Reporting
The media plays a dual role in cases of digital abuse: it can be a powerful tool for raising awareness and holding authorities accountable, but it can also cause immense secondary harm to victims through insensitive or unethical reporting.
The Legal and Ethical Red Lines
- Anonymity is Non-Negotiable: As per Section 228A of the IPC, publishing any information that could lead to the identification of a victim of a sexual offence is a punishable crime. This includes their name, photo, address, workplace, or even family details.
- Avoid Sensationalism: Media must avoid using prurient or sensational headlines and language that blames the victim or focuses on titillating details of the crime. The focus should be on the criminal act and the systemic issues.
- Do Not Share the Material: It is illegal and unethical for media houses to describe, link to, or show even blurred or pixelated versions of the non-consensual material. Doing so contributes to its circulation and the victim's trauma.
- Respect Privacy: Journalists should not hound the victim or their family for interviews or comments. The victim's right to privacy and to heal must be respected above the public's curiosity.
Part XXVII: Frequently Asked Questions (FAQ)
Q: What if the video was taken with my consent but published without it?
A: This is still an offence. Consent is specific and not transferable. Consent to capture an image or video is legally distinct from consent to publish or distribute it. Section 354C of the IPC (Voyeurism) and Section 66E of the IT Act can be invoked, as the act of dissemination breaches your privacy.
Q: The perpetrator is anonymous or using a fake profile. What can I do?
A: Law enforcement agencies have the power to unmask anonymous users. When you file an FIR, the police can legally compel social media platforms and Internet Service Providers (ISPs) to disclose the IP address logs and user registration details (like phone number or email) associated with the fake profile, leading them to the real person.
Q: What if the person who published the video lives in another country?
A: The IT Act has extra-territorial jurisdiction (Section 75), meaning Indian law applies if the crime impacts a person or computer in India. Enforcement requires international cooperation via a Mutual Legal Assistance Treaty (MLAT) or a Letter Rogatory (LR), which is a formal process but very much possible for serious crimes.
Q: Can I file a criminal case and a civil case at the same time?
A: Yes, absolutely. The two proceedings are independent and serve different purposes. The criminal case aims to punish the offender (imprisonment, fine), while the civil case aims to compensate the victim for the harm suffered (damages) and prevent future harm (injunction). They can proceed simultaneously.
Q: What should I do if the local police are uncooperative or refuse to file an FIR?
A: You have several options. You can send a written complaint via registered post to the Superintendent of Police (SP) of the district. If there is still no action, you can file a private complaint before the Magistrate under Section 156(3) of the CrPC, and the court can order the police to register the FIR and investigate.
Q: How does the new Digital Personal Data Protection (DPDP) Act, 2023, help victims?
A: The DPDP Act strengthens your rights significantly. Non-consensual publication of your video is a clear "personal data breach." You have the right to demand its erasure from platforms. Platforms (as "Data Fiduciaries") have a legal duty to protect your data and can face penalties of up to ₹250 crore for failing to prevent a data breach.
Q: I'm the victim of a deepfake video. How can I prove it's not me?
A: The burden of proof is on the prosecution to prove the video is authentic, not on you to prove it is fake. However, you can assist by providing evidence of your whereabouts at the time the video was allegedly made. Further, police can use forensic experts to analyze the video for digital artifacts, inconsistencies in lighting, and other tell-tale signs of AI manipulation.
Part XXVIII: Conclusion: Your Path to Justice and Recovery
The non-consensual publication of a private video is a deeply violating act designed to shame, control, and silence. It is a digital weapon that attacks one's most fundamental rights to privacy, dignity, and self-determination. However, as this comprehensive guide has demonstrated, silence is not your only option. The law, while complex, is a powerful ally.
You are equipped with a multi-layered defence system: the constitutional shield of the Right to Privacy, the punitive sword of the Indian Penal Code and IT Act, the restorative power of civil lawsuits, and the accountability framework of the data protection laws. From the immediate relief of a takedown notice to the long-term justice of a court conviction, a clear path exists.
Navigating this path requires courage and a strategic approach. It begins with the crucial first steps: preserving every piece of evidence, reporting the crime without delay, and refusing to yield to threats or blackmail. It involves understanding that the fight is not just in the courtroom but also in the mind, making mental health support an indispensable part of your recovery.
Technology will forever be a double-edged sword, creating new threats as it opens new possibilities. But the principles of justice are timeless. By understanding your rights, leveraging the available resources, and taking decisive action, you are not just a victim; you are an agent of your own recovery and a force for accountability. You have the power to reclaim your narrative, erase the digital shadow, and move forward with strength and resilience.